Non-professional address
Professional companies use their own domains for their e-mail addresses instead of using free mail services, e.g.: support@twitter.com instead of twitter@yahoo.com.Read more...
Let’s say, you received an e-mail seemingly from Twitter. If you don’t know already, you quickly find out that their domain is called twitter.com . Now, what’s the sender’s e-mail address? Let’s say it’s support@twitter.com . The domain is the part behind the @ symbol, so in this case it’s twitter.com . That definitly seems legit.
But what if the sender is twitter@mail.com ? There’s the word “Twitter” in it too. The difference is: It’s just a random user name which is not unique. The domain is mail.com , a popular e-mail provider for private users. A company like Twitter would never use such an unprofessional mail service when they could use their shiny twitter.com domain.
Fake support of free e-mail service
Some scammers don’t try imitating a company by using a free service like with the twitter@yahoo.com example above. Instead, they try to imitate the free e-mail service itself , e.g.: friendly-user-support@yahoo.com . This seems to be Yahoo’s actual customer support but it’s actually just a random user account that happens to have a “weird” user name. That’s why you should always google whether the sender’s e-mail address actually belongs to your e-mail service’s support.Wrong account address
A fraudster usually doesn’t know which e-mail address belongs to which online account (or vice versa) so you may receive a phishing e-mail seemingly from Amazon to an e-mail address of you which doesn’t belong to your actual Amazon account. And as Amazon would never ever send any e-mails to addresses that don’t belong to the respective user account you can be quite sure that e-mails to the wrong address are actually phishing attempts.Messages from services you don’t use
Scammers just imitate any popular company/service out there because then the chances are quite high that the randomly chosen victim actually uses the respective service. But let’s say, you receive an e-mail from TikTok but you don’t even use TikTok – then it’s obviously a fake.Sub-domain instead of domain
Some scammers buy own domains for their e-mail addresses and make them look like legit ones, e.g.: support@amazon.com.beispiel.de . It looks like the domain was amazon.com but it’s beispiel.de instead.Read more...
Every web address consists of several parts. Basically, it’s this scheme:
Example: https://pixelcode.codeberg.page/phishwarn/index.html
For e-mails, only this part is relevant: subdomain.domain.TLD
The important thing about this is that every domain.tld is unique. There’s only one ebay.com and only one freedom.press.
On the other hand, sub-domains are NOT unique . Every owner of a domain can set any sub-domain he likes and as many sub-domains he likes. That’s why an e-mail domain like this one could be possible: amazon.com.beispiel.de .
Note that the actual domain is NOT amazon.com but beispiel.de instead. However, many users wouldn’t know that amazon.com isn’t the domain and think that the sender actually is Amazon when instead, amazon.com is just two sub-domains: amazon and com.
The real domain is always the last string before the top-level domain. The TLD is something like .com, .net, .gov.uk, .de, .fr etc. If you aren’t sure about this domain stuff, just remember that many dots within an e-mail domain is suspicious = many sub-domains.
High pressure on you
Scammers put high pressure on you, using urgency or severe consequences and pretending to be important authorities.Read more...
1. Urgency: If you’re told to do a specific action within e.g. 24 or 48 hours, you should probably wait a minute. Ask yourself: Does the issue really seem that urgent? Would the real sender send such an important message to you via e-mail/SMS etc.? Why wouldn’t they send you a letter to ensure you receive their message?
2. Severe consequences: If you’re threatened with severe consequences like an account ban, or being sued, arrested or fired, it’s the same situation: Would the real sender threaten you like that – especially via e-mail/SMS etc.?
3. Important authority: Many fraudsters claim to be someone like your doctor, the police, the government in general or any other important authority. Stop for a moment and think about whether you’ve ever received a message from the respective sender via the means of communication used. If not: Are you sure that __the police__ would send you an e-mail? Do they even know your address? Why would they choose such an insecure means of communication when they could’ve sent a letter?
At least in the Western world, police would never ever send e-mails or text messages but letters instead. In urgent cases, they would send police officers to talk to you in person.
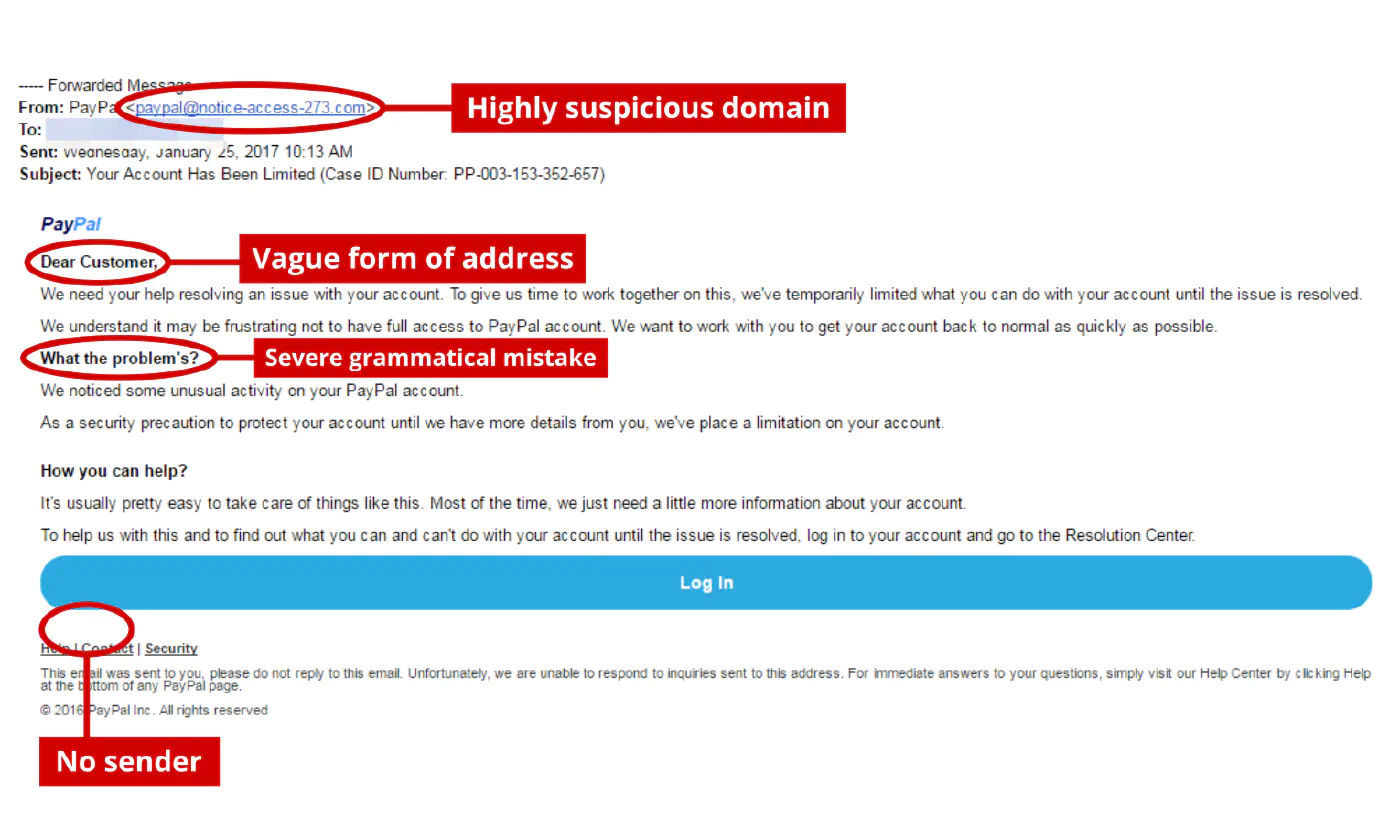
Vague form of address
Many fraudsters use vague forms of address instead of your actual name because they simply don’t know it. For example, a bank would never use something like “Valued customer...” or “Dear Sir or Madam...” in a message with customer-specific contents. So if the sender doesn’t mention your name but should know it if he was actually legit, then you should be alert.Poor grammar and spelling
Some phishing messages contain many and severe grammar and spelling mistakes – unlike legit messages from professional companies that ensure they don’t damage their reputation.Read more...
1. Bad online translation: Many scammers use online translation services of low quality to distribute their phishing messages in different languages. Google Translate’s poor quality has even become an internet meme.
2. Not a native speaker: Many scammers simply come from foreign countries where the victim’s mother tongue isn’t a lingua franca. Many of them also come from poor regions of the world where there’s no proper education in general.
3. Efficiency: It might be more efficient to send out thousands of phishing mails without proper grammar than manufacturing a few high-quality mails.
4. Poor education: People who have to rely on scamming to earn money may have a poor education just like many regular criminals.
However, note that recently, there have been some phishing messages of good grammar. So don’t rely on poor language as a warning signal.
Disguised links
Usually, fraudsters disguise their phishing links by choosing a unsuspicious display texts, e.g. “www.wikipedia.org” as the display text for example.com as the actual link: www.wikipedia.orgRead more...
So scammers choose as the visible display text for example “www.amazon.com/gp/customer-service ”, but link to a phishing site instead, e.g. example.com (this one is obviously harmless). That looks like this: www.amazon.com/gp/customer-service
But how to recognize this? All major browsers will display the link URL at the screen’s bottom when hovering over the link. Try it out: example link
Only concentrate on the URL preview (not on the possibly faked display text) and determine whether it’s trustworthy or not. If you don’t know, do NOT click on the link.
Foreign language
Some scammers simply don’t know or don’t care about their victims’ mother tongues so that for example a German may receive a French phishing mail from his/her German bank. Why would the bank translate their message into a foreign language that their customer probably doesn’t even speak? That wouldn’t make any sense.Request for sensitive user data
The fraudsters’ goal is acquiring the victims’ login credentials and other personal data which is why they openly ask about passwords, PIN numbers or TAN codes. Legit companies, however, would never ever ask about sensitive user data in an e-mail or a chat message because that’s highly insecure. Also, customer supports do NOT need the user’s password as they have full access to the company’s user database.Attachments and calls to action
All phishing messages ask the victim to execute certain instructions, such as klicking on a link or pressing the big shining button. Many scam mails also contain attachments of malicious content (more about that below). Although real emails also instruct the user to do certain things, they are usually far less aggressive or demanding and are not necessarily limited to links and buttons. On the other hand, it is not that common for the real support to send an attachment.Executable file
Some scammers also try to make the victim download a program or application by telling him/her to download and install an attached .exe, .msi, .app or .apk etc. file. Often, such files are also disguised as harmless (e.g. “dispatchconfirmation.pdf.exe” ) or hidden from spam filters in a ZIP file.Read more...
You should never open, download or install anything mentioned in a suspicious e-mail.
Caution! Many executable files are not recognisable as such! Just like phishing websites are disguised with seemingly legit sub-domains, fraudsters try to disguise the file type of attached executable files by naming them for example “billing.pdf.exe” or “holidayphoto.jpg.app” . In this case the actual file types are .exe and .app – and NOT PDF resp. JPG.
Also, may e-mail programs don’t display the file type by default which is why “billing.pdf” would be displayed instead of “billing.pdf.exe” – which fatally doesn’t look suspicious at all!
Moreover, some scammers hide their executable files inside of .zip archives to prevent e.g. spam filters from detecting the suspicious .exe attachment. If you’re seeing a ZIP file attached you should take extra care!



